
The Critical Security Controls at the Gartner Security Conference | SANS Institute | Security conference, Cyber security, Security
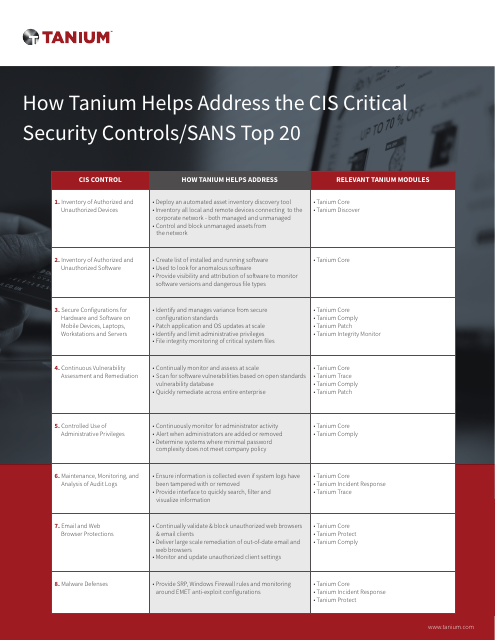
How Tanium helps address the CIS Critical Security Controls/SANS Top 20 | Cyentia Cybersecurity Research Library

SANS Institute on Twitter: "The @CertifyGIAC #GCCC is the only cert based on the Critical Security Controls, a prioritized risk-based approach to security. Get help preparing to certify w/ associated course, SANS #
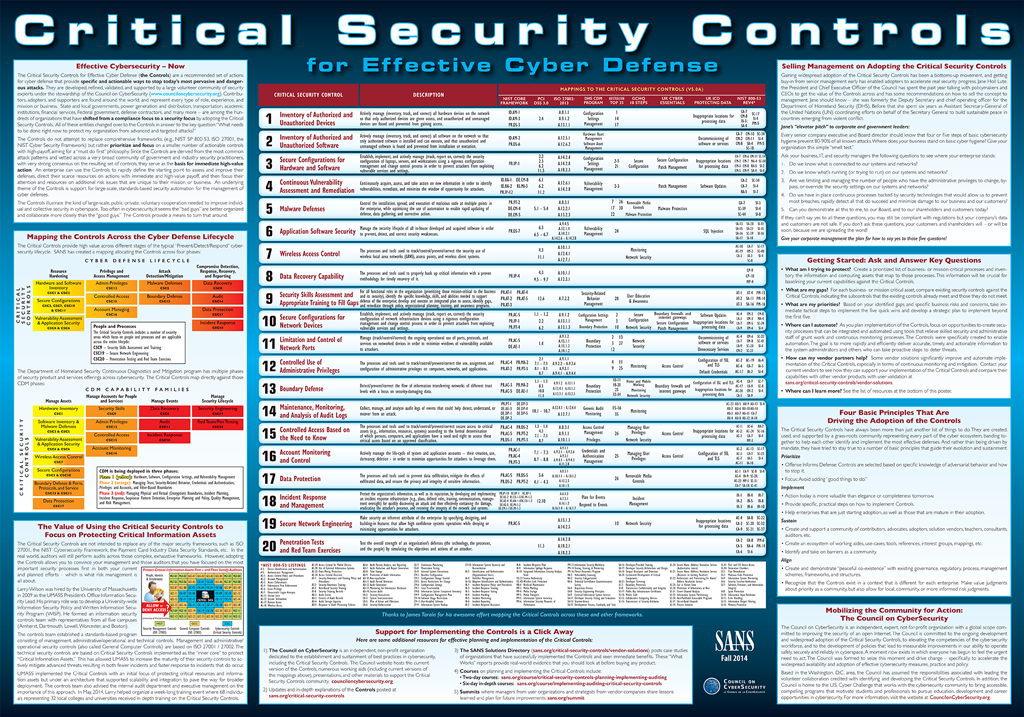
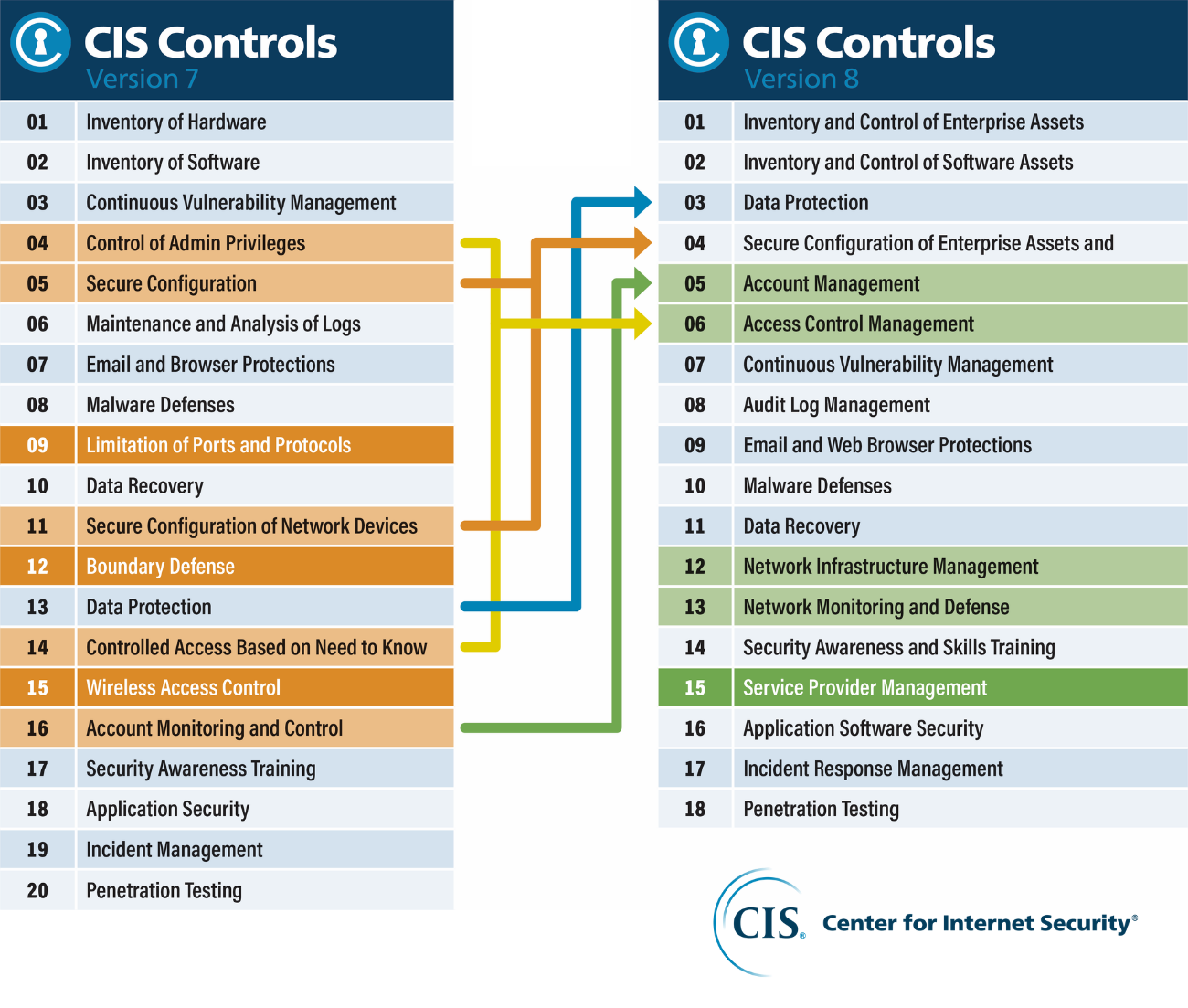







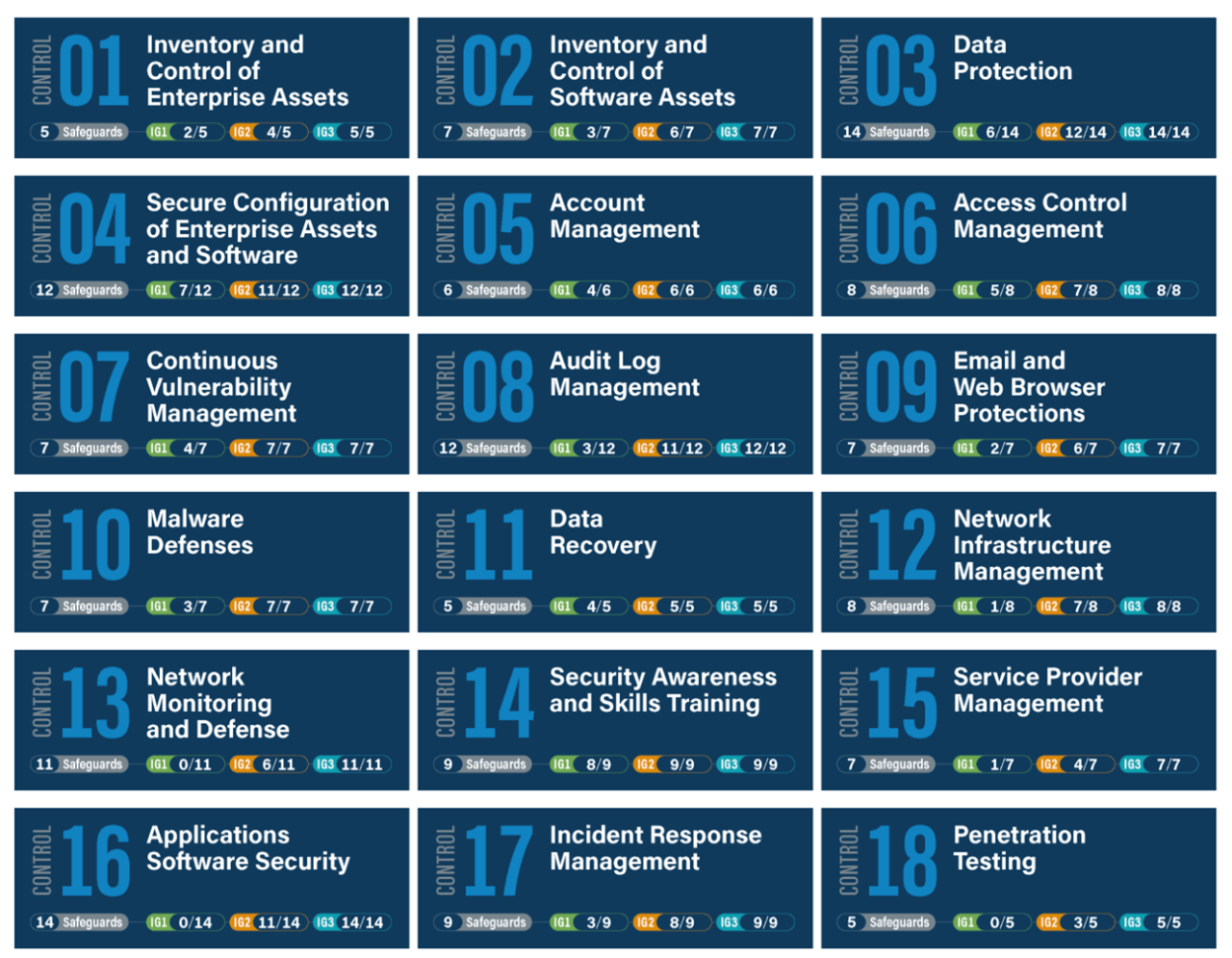








:quality(90)/images.vogel.de/vogelonline/bdb/1160700/1160739/original.jpg)